Courtesy of PEI
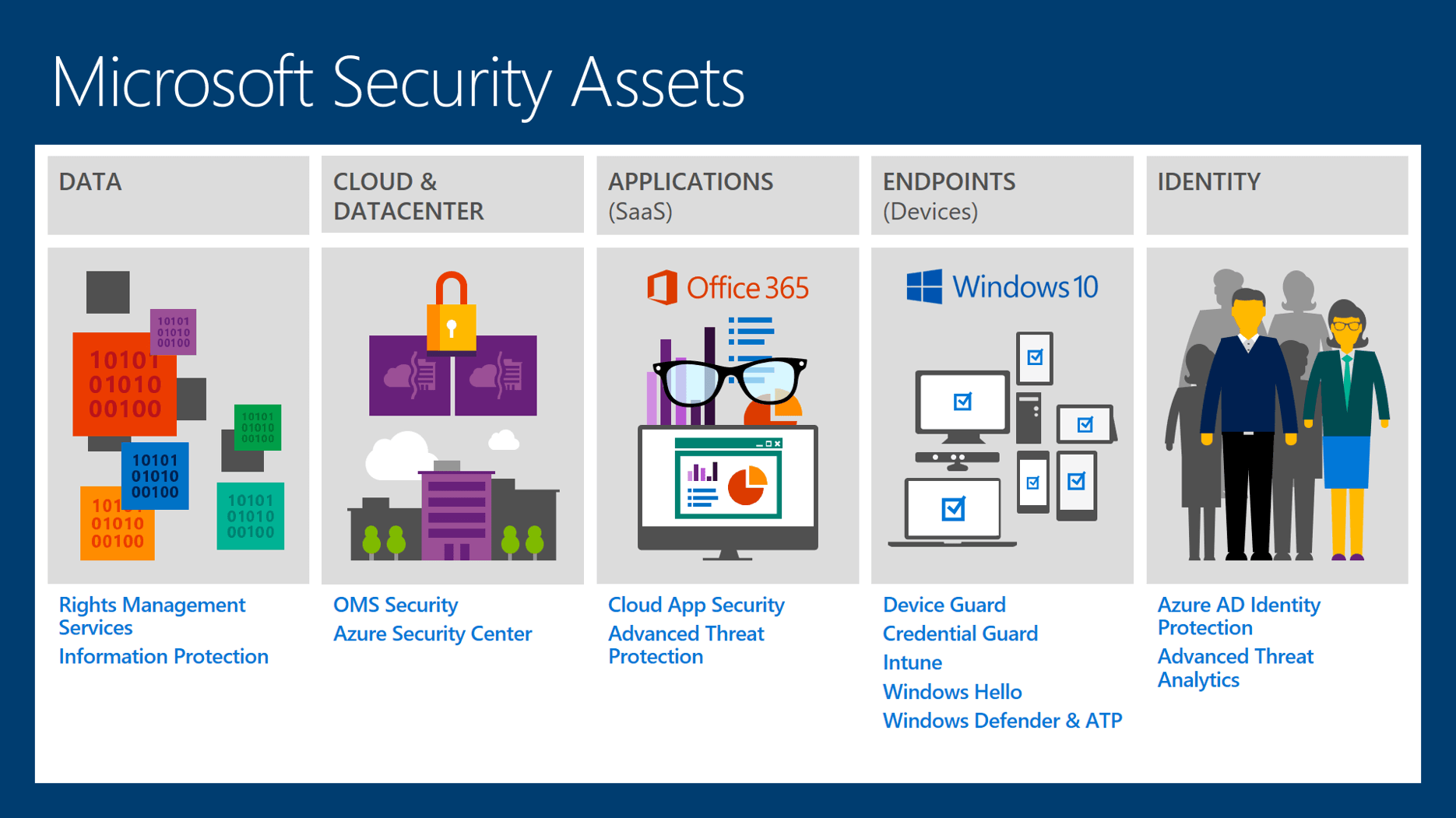
As the world continues to adapt to the evolving threat landscape, Microsoft has taken significant action in enhancing their focus on security. They understand the world their clients live in and continuing to stay ahead of threats allows Microsoft to ensure their cloud-based solutions are both up to date and protected. Microsoft continues to invest in five main pillars for security—Data, Could & Datacenter, Applications, Endpoints, and Identity–and staying current with the offerings can be challenging. This blog is geared towards providing some education on the different areas of security Microsoft is focusing on and providing some clarity on the specific solutions available to organizations today.
Data
Microsoft sees the value in ensuring organizations and users can control access to sensitive data and have aimed their solutions at achieving that level of control. Rights Management Services allow users and organizations to lock down documents, emails, files, etc. to provide that security layer. There are a few different focus areas for Rights Management, so I’ll outline a few use cases.
Azure Information Protection
Azure Information Protection can control and help secure email, documents, and sensitive data that you share outside your company. From easy classification to embedded labels and permissions, AIP can enhance data protection at all times—no matter where it’s stored or who it’s shared with. This is a part of the Microsoft Enterprise Mobility + Security solution, and is available in different bundling packages.
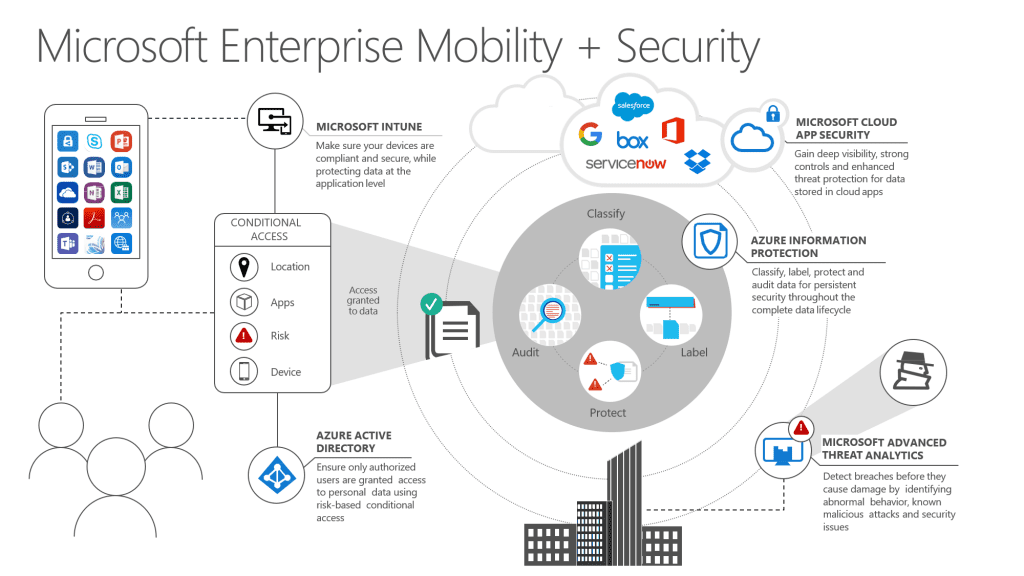
Azure Rights Management
This solution is a combination of Information Rights Management (IRM) and Office 365 Message Encryption.
Information Rights Management (IRM):
Help protect data across different workloads such as SharePoint, Exchange, and Office documents by easily applying Information Rights Management to set up policy-based permissions rules.
- Help protect emails against unauthorized access by applying different IRM options to your email messages.
- Enhance the security of your SharePoint libraries by using IRM to set up appropriate permissions.
- Help keep your information safe–online or offline–because your files are protected whether they’re viewed using Office Online or downloaded to a local machine.
- Seamless integration with all Office documents helps guard your organization’s intellectual property.
- Apply custom templates based on your business needs in addition to using default Rights Management Services templates.
 Office 365 Message Encryption:
Office 365 Message Encryption:
Deliver confidential business communications with enhanced security, allowing users to send and receive encrypted email as easily as regular email directly from their desktops.
- Safely share files in email or Microsoft OneDrive, independent of which mail service the recipient uses.
- Grow your organization’s brand by enhancing the contents of the mail and your users’ experience with your custom logo or disclaimer.
- Strong integration with Exchange transport rules allows you to set up encryption/decryption using a single action.
- The clean Office 365 user interface makes it easier to read, review, respond to encrypted mail.
- Help protect the entire conversation by encrypting an entire email thread without requiring any service subscription for recipients.
I’ve provided an example below of the permissions an end user is able to set on an outgoing email.
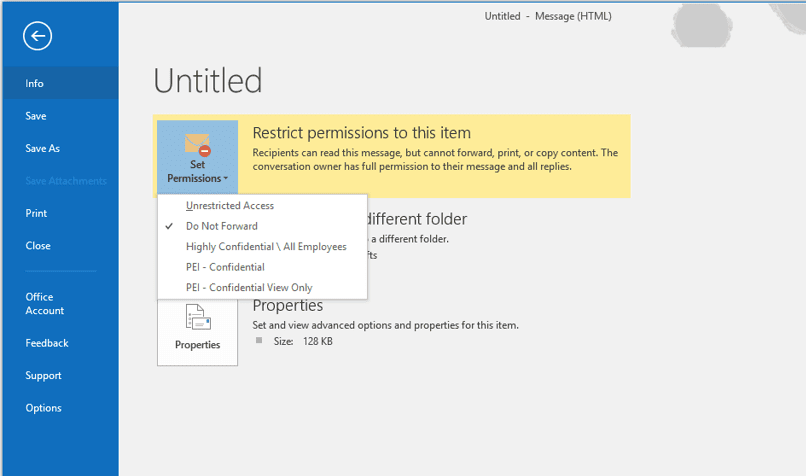
Data Security Resources:
Not sure how strong your security practice is? Contact us today for a Security Assessment to identify potential vulnerabilities in your environment!
Cloud & Datacenter
As organizations continue to increase consumption of cloud services, Microsoft understands the need to have a wholistic approach for organizations to secure their hybrid environment. As such, Microsoft has built out the Operations Management Suite (OMS) and Azure Security Center to address these needs. For anyone who hasn’t heard of or looked at OMS, it’s a remarkably powerful toolset that has not garnered the level of attention it deserves. For organizations that are moving quickly to Azure’s Infrastructure as a Service capabilities, this solution provides incredible capabilities around monitoring, compliance, automation, insight, and data protection/recovery. This blog would go on forever if I dive into all facets of OMS, so I’ll give a brief overview for each component and dive a little deeper into the security side.
Operations Management Suite
OMS is made up of four primary components:
- Insight & Analytics: Gain Visibility across workloads with access to all the information needed on what’s happening in the environment
- Automation & Control: Enable consistent control and compliance through configuration, update management, and advanced change tracking
- Protection & Recovery: Ensure the availability of important applications and data, and keep critical data protected with integrated cloud backup and site recovery
- Security & Compliance: Drive security across the environment, with sophisticated threat intelligence capabilities, malware detection, and indicators of compromise
For organizations that enable and configure OMS Security, leadership will have a holistic view of their security state—from on-premises to cloud and across Windows and Linux systems. By helping ensure your environments are configured and operating securely, OMS Security will empower organizations to more effectively defend against cyber threats. In addition, by using advanced security analytics and threat intelligence, the solution can detect attacks earlier. Once deployed, the management team can quickly search large volumes of security data and use built-in threat intelligence to enable smarter investigations.
 By configuring OMS Security and Compliance, organizations will meet the following objectives:
By configuring OMS Security and Compliance, organizations will meet the following objectives:
- View the security posture of the organization’s entire environment and quickly identify issues such as missing security updates, outdated antimalware, vulnerable OS configurations, and unusual access or network activity
- Leverage advanced security analytics and Microsoft threat intelligence to detect attacks in near real-time
- Reduce investigation time with built-in threat intelligence and rapid search of the organization’s security data
- Use security data and insights to demonstrate compliance and easily generate evidence for auditors
Azure Security Center
Unified security management and advanced threat protection across hybrid cloud workloads. By working in unison with OMS Security & Compliance, customers can start using Security Center to unify security management and threat protection across Azure, on-premises, and other clouds.
Azure Security Center now includes the same security management capabilities currently available in the OMS Security & Compliance solution, including:
- Secure data collection, search, and analysis
- Notable events driven by predefined and custom queries
- Security assessment dashboards, including system update status, antimalware protection state, OS baseline configurations, and identity and access
- Inventory of connected computers
- Advanced threat detection
- Interactive threat intelligence map
 In addition, Security Center offers:
In addition, Security Center offers:
- Security policies to ensure compliance with company and regulatory security standards
- Actionable security recommendations to help mitigate security vulnerabilities
- Automatic discovery and monitoring of new Azure resources
- Additional security assessments for Azure services, including monitoring of VM, network, storage, and SQL configurations
- Adaptive application and just-in-time access controls for Azure virtual machines
- Security incidents and streamlined investigation for rapid threat response
As with all things Microsoft, there are a couple different ways to license OMS and Azure Security, and PEI is more than happy to assist with building the best route for your organization.

Leave a comment